Firewall/IDS Lab Lab [10 points]
These exercises are based heavily on those developed at Seed Labs.
Exercises
-
[2 points] Start two VMs, machine A and machine B. Use iptables on machine A to create a packet filter firewall on machine A that prevents A from telnetting to B and B from telnetting to A. Telnet uses port 23. Demonstrate that you cannot telnet between machines.
Also implement a rule to prevent machine A from visiting Facebook by blocking outbound traffic to that site (hint: you'll need to determine Facebook's IP address first). Show that you can reach other Internet sites using Firefox, but not Facebook. Once you've demonstrated you can block Facebook, clear your Facebook rule, but keep the telnet restrictions. Show that you can reach Facebook.com again, but still cannot telnet between machines.
Submit the commands you entered to create the firewall and screen shots/output showing the desired behavior.
-
[4 points] Reestablish the rules from above that block telnet and access to Facebook. Demonstrate that you cannot reach Facebook from machine A. To evade the Facebook rule, we can enlist another machine to help using secure shell (ssh). SSH can set up a connection between machines similar to telnet, but unlike telnet, ssh encrypts the data exchanged.
Create a secure shell from machine A to machine B by using the following command on machine A:
This will create a secure shell connection between machine A and machine B using port 9000. You'll be asked to log in with machine B's password (dees) to finish the connection.ssh -D 9000 seed@<IP of machine B>SSH uses port 22 which is not blocked by the firewall rules you've created and will be allowed. Once the ssh connection is established, we want to use it to route our request to Facebook from machine B (which does not have a firewall rule prohibiting access to Facebook like machine A does). To achieve that, we can tell Firefox on machine A to use localhost:9000 as its web proxy. We need to ask Firefox to connect to localhost:9000 every time it needs to connect to a web server, so the traffic can go through our SSH tunnel and out machine B. To support this dynamic port forwarding, we need a special type of proxy called SOCKS proxy, which is supported by most browsers. To set up the proxy in Firefox, go to the menu bar, click Edit -> Preferences, scroll down to Network Proxy, and click the Settings button and make these changes:
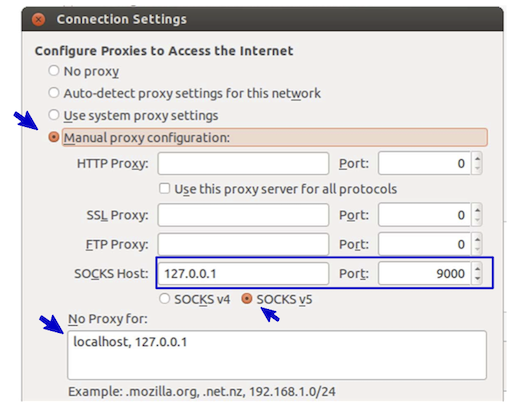
After the setup is complete, do the following:
- Run Firefox on machine A and visit Facebook. Can you see the Facebook page? Describe your observation
- After you get the Facebook page, break the SSH tunnel, clear the Firefox cache, and try the connection again. Describe your observation
- Establish the SSH tunnel again and connect to Facebook. Describe your observation
- Explain what you have observed, especially on why the SSH tunnel can help bypass the egress on machine A. Use Wireshark to see what exactly is happening on the wire. Please describe your observations and explain them using the packets that you have captured.
Finally, clear all firewall rules.
Submit your observations and the commands you entered.
-
[4 points] Install the snort Intrusion Prevention System (IPS) system on your VM (take a snapshot before installing) using the instructions from class. This installation is very sensitive to packets sent to the machine running snort. Use nmap on another VM to do a scan the network to enumerate all hosts on the network. Next, run a nmap scan of the machine running snort using:
- -sT flag
- -sS flag
- -sS -D 1.2.3.4
- -sS -T2 (Note: -T2 will take a long time to run, you can see its progress by hitting the space bar while it runs)
- -sS -T3
Show and explain the difference between the -sT and -sS (no extra parameters) flags in Wireshark (you need only show a screenshot of the first few packets exchanged). Why might the -sS flag draw less attention from an IDS?
Describe the differences in snort's alerting to the various flag combinations. Was snort fooled by the -sS (stealth) scan? What is the advantage of using the -T2 vs. the -T3 flag for an adversary. Were you able to scan the machine without snort raising an alarm? Describe any differences in the services discovered to be running on the target machine by the various scans. Is this result expected?
Submission Instructions
Create a single .pdf file with your answers to these exercises. Zip your code files together with your .pdf into a single file and submit that file via Canvas. In the text box on your Canvas submission, provide the names of your partners. Only one partner need submit.
Grading rubric
Exercise 1 [2 points]: Create a packet filter firewall using iptables
- 1 point: Block telnet in both directions
- 1 point: Block Facebook.com.
Exercise 2 [4 points]: Evade the firewall using ssh
- 1 point: Create the ssh tunnel to a second machine
- 1 point: Set up Firefox to use the tunnel when making web requests, demonstrate success reaching Facebook
- 2 points: Describe your experiences.
Exercise 3 [4 points]: description
- 1 point: install snort
- 1 point: run a nmap scan of the network, show all live hosts
- 2 points: run nmap scans using the flags shown and describe the differences in scan behavior as requested.