APImote: a platfrom for low-level 802.15.4 experimentation
 |
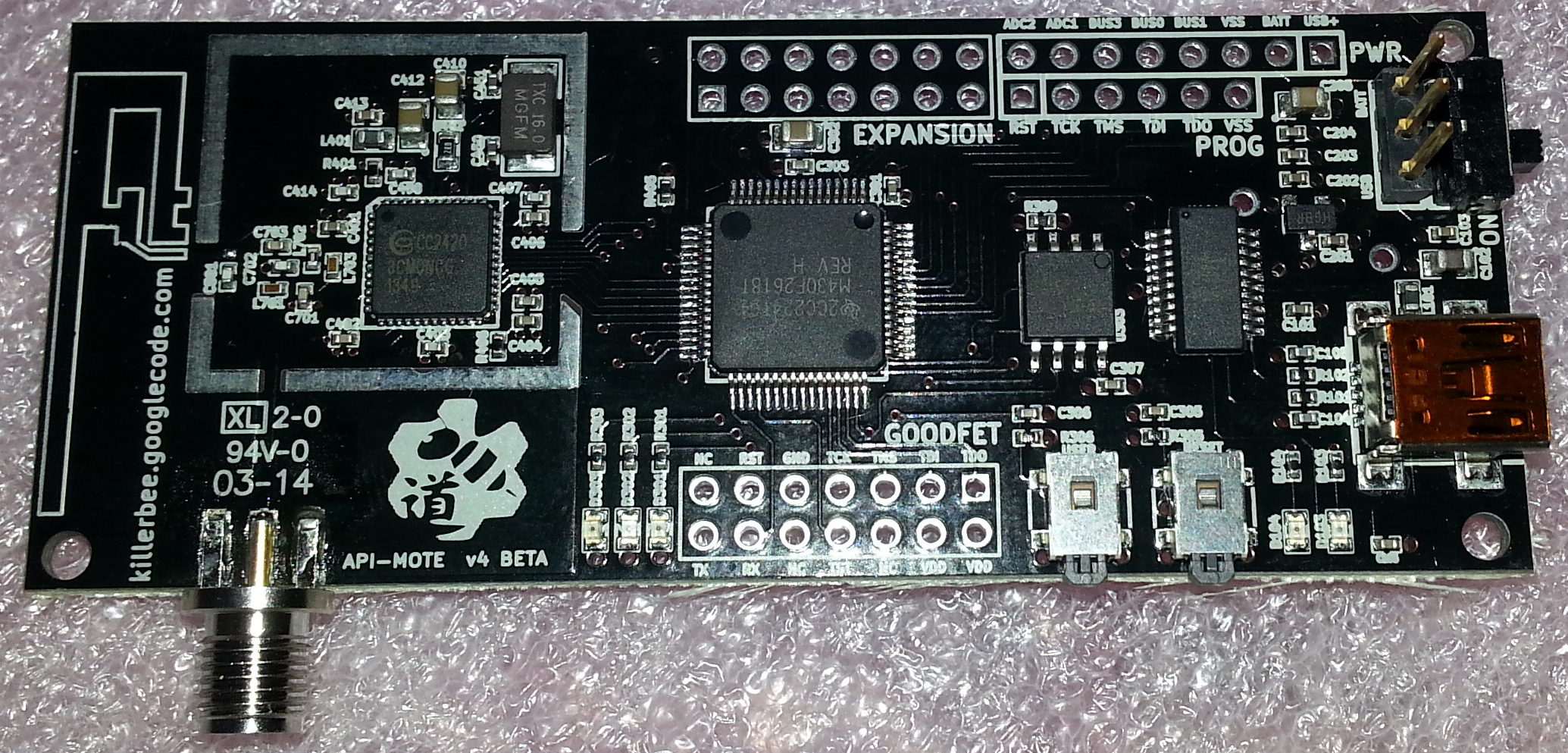
APImote is a USB peripheral for experimenting with raw 802.15.4 frames. APImote aims to make raw frame sniffing and injection easy, with Python and Scapy where timing isn't critical (but see discussion on reflexive jamming in the API-do paper below). |
The APImote hardware was designed by River Loop Security in collaboration with the Dartmouth Trust Lab and Travis Goodspeed.
APImote is open-source hardware: ApiMote hardware designs.
APImote was inspired by Wright's Principle,
Practical security does not improve until tools for exploration of the attack surface are made available. —Joshua Wright, Toorcon 11, 2009,and works with the KillerBee 802.15.4 software suite (now maintained by River Loop).
Papers & talks about APImote
"ApiMote: a tool for speaking 802.15.4 dialects and frame injection", Defcon Wireless Village 2014 talk.
"Api-do: Tools for Exploring the Wireless Attack Surface in Smart Meters" (but not just for smart meters!),
paper at Hawaii International Conference on System Sciences/IEEE Computer Society, 2011.
"Making (and breaking) an 802.15.4 WIDS", Troopers.de 2014 talk, [slides], [video].
"ZigBee Security: Find, Fix, Finish", ShmooCon 2011 video [1], [2].
"802.15.4/ZigBee Analysis and Security: Tools for Practical Exploration of the Attack Surface", Dartmouth TR2011-689 technical report.
Papers & talks in which APImotes helped
"Packet-in-packet", or how to inject 802.15.4/ZigBee digital radio frames without owning a radio: [pdf] [blog] (USENIX WOOT 2012)
"1/8th of a nybble", in which we evade anti-PIP measures that filter some strings before transmission, by shifting the signal so that transmitted and received frames have no bytes in common: [pdf] (1st LangSec IEEE S&P workshop 2014)
"Digital radio dialects & shaped charges", in which we use dialects of 802.15.4 PHY frames to inject frames invisible to some RF chips no matter what the signal-to-noise ratio is: [pdf] (ACM WiSec 2014)
"DemystiPHY 802.15.4", on how RF dialects arise: [slides] (InfoSec South West 2014), [video] (invited talk at Dartmouth)
See also: BabylonPHY.